JSC Exploits
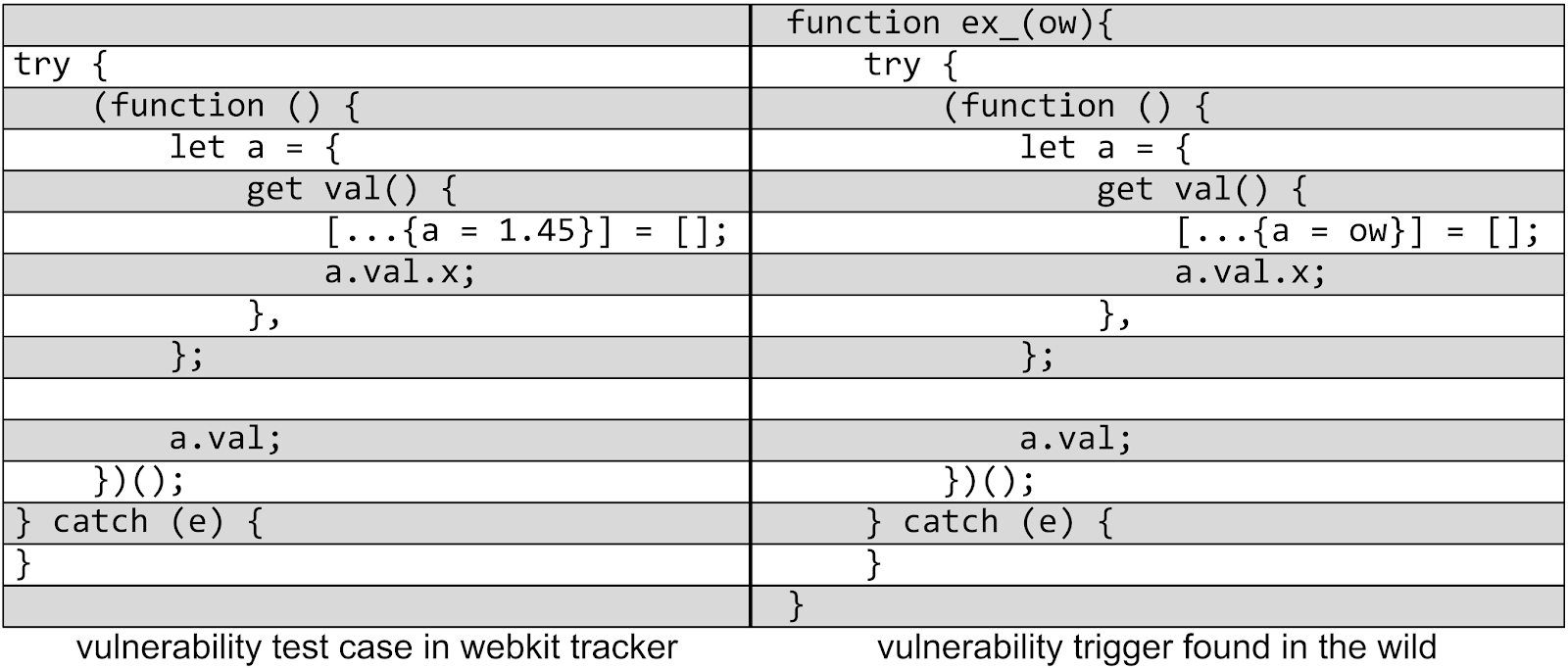
In this post, we will take a look at the WebKit exploits used to gain an initial foothold onto the iOS device and stage the privilege escalation exploits. All exploits here achieve shellcode execution inside the sandboxed renderer process (WebContent) on iOS.
from Pocket https://ift.tt/2PDM8if
via IFTTT